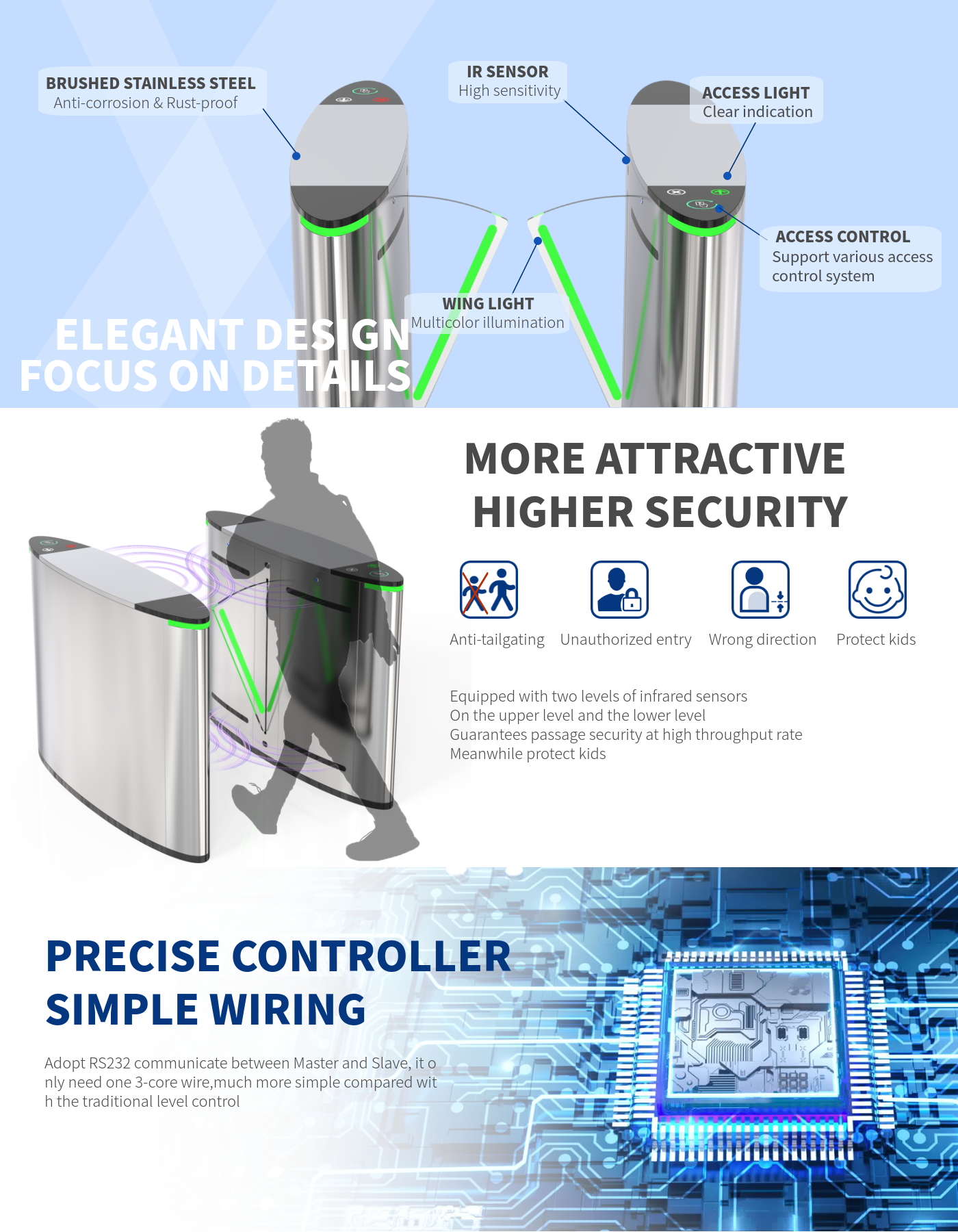
Flap Barrier
Flap barrier is a control device for the passage of people. It is used in places where personnel control is required for exits and entrances, such as canteens, hotels, museums, gymnasiums, clubs, subways, stations, and docks. Flap barriers can make people